There will often be a need to onboard clients/devices that don’t support eat-tls or similar 802.1x authenticatios methods. This could be scanners, POS’s, Solar panels or typically IoT devices. To have these devices associated to the Wireless Network, often PSK is used. The iisue is that PSK is shared among devices and can easily be compoimised. A way to have these devices onboarded in a more secure manner, is to use iPSK (This is the Cisco way with ISE/NPS or other radius). Other vendors, like Aruba has an built-in device portal, that can be used to have devices onboarded de-centralized. (There is a iPSK manager project on github. More on that later…). The diagram below shows the general flow of traffic when using iPSK to authenticate against a Cisco ISE server.
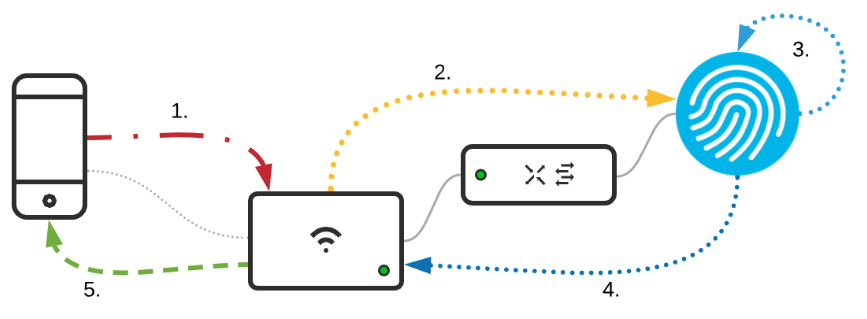
- Clients authenticates and associates to WLAN
- Upon authetication/association AP sends Radius MAB request to ISE
- This can alsp be profiling in ISE
- ISE processes MAB/Profiling through Policy Sets
- ISE responds back with PSK
- AP and client complete 4-way handshake
Here are som usecases where i have implemented iPSK:
- A large number of devices like: internet radios, Televisions, Fitness equipment etc. In ISE a group have been made for different type of equipment. Every group have a uniq PSK and send out a VLAN attribute. When provided with MAC and equipment type, this is configured in ISE. Afterwards device can be onboarded with PSK for group and will be onborded into correct vlan.
- Large Company with hundreds of shops which have all kind of legacy and IoT devices. Using existing Wireless Infrastructure which provide a iPSK WLAN (configured in ISE), where these devices are onboarded and provided with correct vlan according to usage/security.
How-To on Cisco 9800 and ISE
On 9800 make an Authorization under AAA Methods List:
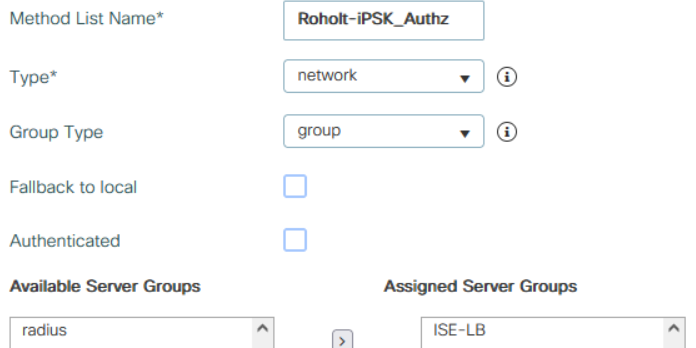
This assumes tha ISE nodes has been setup on WLC “ISE-LB”
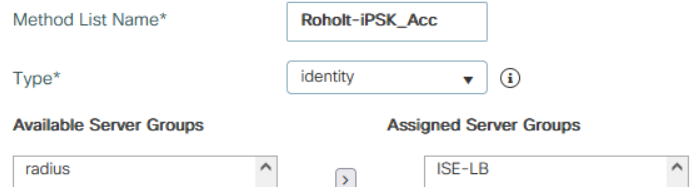
If you want accounting also define that:
9800 WLAN Profile
Create a PSK WLAN with MAC Filtering enabled pointing to the Authorization created:
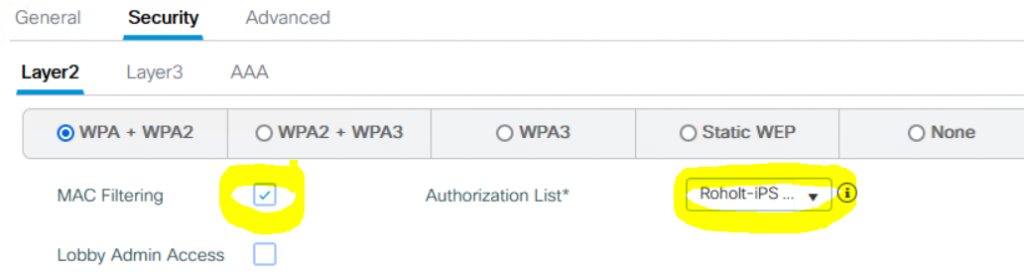
PSK defined is not going to be used for authentication, so just make one up.. OR if you want a kind of “last resort” possibility and configure ISE to allow it, it actually can allow clients with PSK matching the one you define here on WLC and tag them into the vlan you define in the Policy Profile.
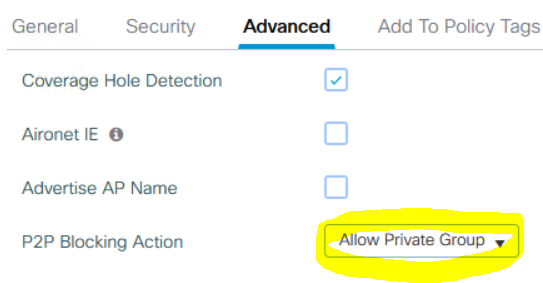
Under Advanced you cab enable Clients in same iPSK group to be able to communicate with each other:
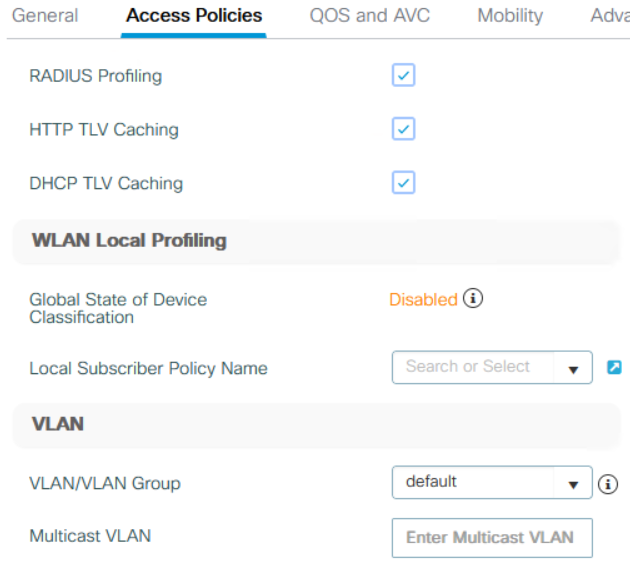
9800 Policy Profile
Determine the vlan/vlan group if using the option defined above.. Othervise tag in a dummy vlan:
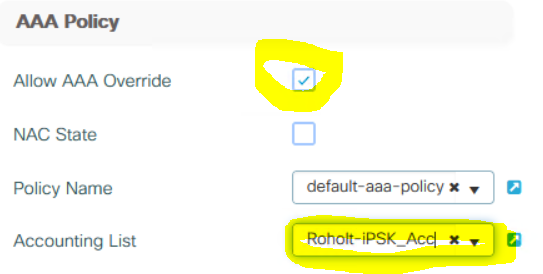
Under Advanced enable AAA Override and if accounting wanted, also Accounting List:
Map Wlan Profile and Policy Profile in a Policy Tag and assign it to AP’s
ISE
In your Policy Set define ex.
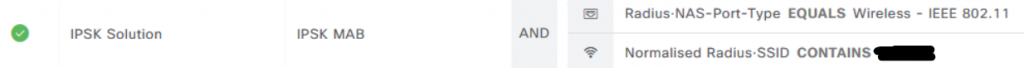
and in Authorization Policy you can define if Clients are forced to use this iPSK groups or have the possibility to use PSK on WLC and being mapped to vlan defined in WLC “Deny or Permet”

And in Authorization Profiles define your vlan, PSK, av-pair etc.
Here is a video showing the essentials of configuring iPSK between 9800 and ISE:
