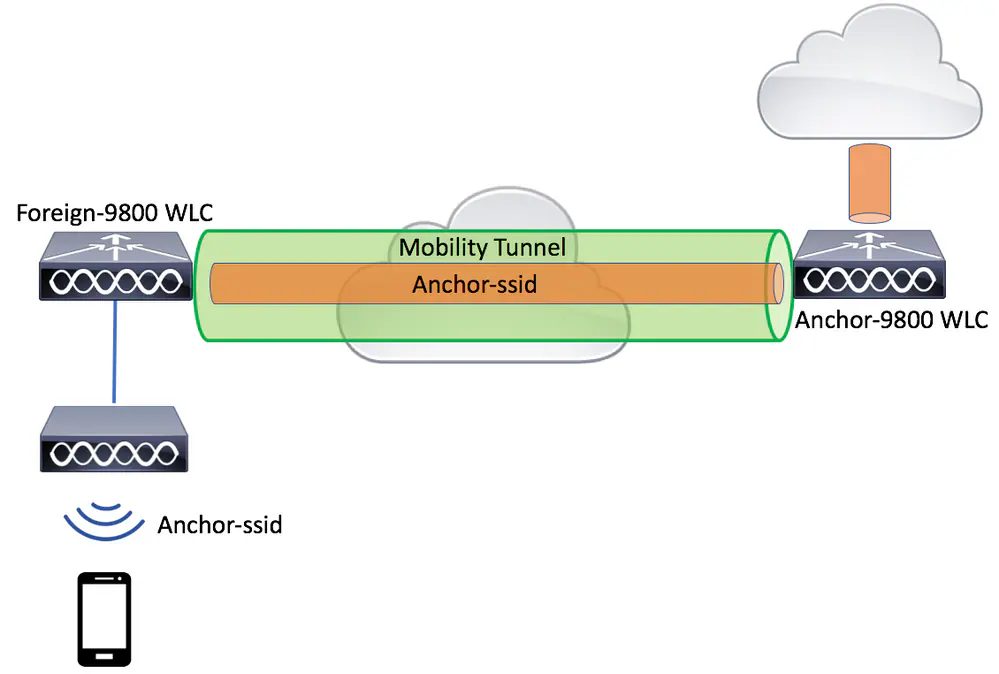
Tunnelling Wireless Client traffic between Controllers is very useful in some scenarios. Have used it for isolating Guest Traffic (typical in DMZ) and in Multi-Company facilities (Two or more companies sharing same locations and need their own Wireless infrastructure in shared areas).
Things to rember:
- Foreign Wireless Controller are where AP’s terminate
- Foreign Wireless Controller handles all radius
- Anchor Wireless Controller are where WLAN are terminated
- Anchor Wireless Controller handles Web-authentication (L3)
- Anchor Wireless Controller handles DHCP (ex. if internal DHCP is needed)
- Between Foreign and Anchor, the following needs to be able to communicate:
- UDP 16666
- Test connectivity with: mping <mobility_peer_IP>
- IP protocol 97
- Test connectivity with: eping <mobility_peer_IP>
- UDP 16666
Note (personally experience): When setup mobility between AOS and IOS-XE, you need to enable “data encryption” otherwise issues with ex. WiFi-Calling.
Note (personally experience): When Firewalls involved between Anchor/Foreign Controllers, and these are inspect tls 1.3, issues occur with ex. MS Teams (not possible to disable tls 1.3) and browsers which use tls 1.3 (possible to disable)
